This tale covers finding artifacts left behind when an SD Card is plugged into a Windows computer.
Overview
This tale was made after investigating a case against an individual storing business data through an SD Card and finding limited resources regarding SD card artifacts. I will preface this that “Secure Digital” is the acronym for SD (I totally did not know this during the time and I felt silly when a friend brought this up to me).
OBJECTIVE: Identify the artifacts found to indicate that an SD card was plugged into the Windows system.
Quick Review of Registry Fundamentals
To ensure that everyone is on the same page within this tale, it’ll be important to go over the fundamentals with registry definition.
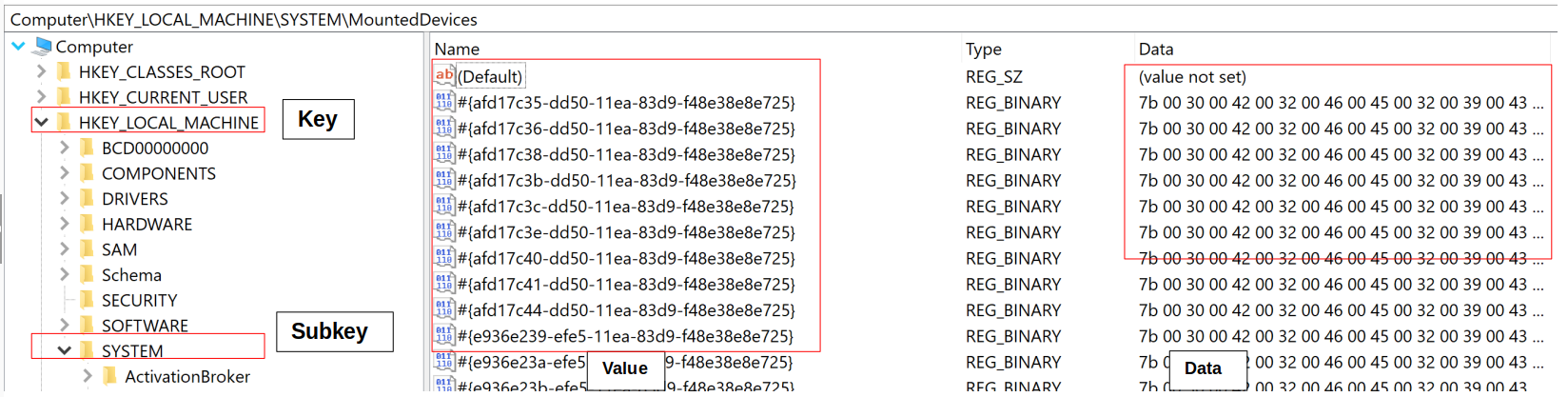
Per Microsoft Documentation, the registry is a hierarchical database and is structured in a tree format.
- Keys: Next level down from a tree which contains at least one subkey (HKLM for this example)
- Subkeys: Next level down from the key or subtree which stores either entries or other subkeys.
- Value: Found within the subkey and is typically assigned data to it
- Data: The entry tied to the specific value.
Validation of USB
Before we go over the SD Card-related artifacts, it is important to review the USB-related artifacts because this provides a good baseline knowlege to pivot from.
Note on the below screenshot, within HKLM\SYSTEM\CurrentControlSet\Enum\USBSTOR , there are detailed information listing the vendor and product model of the device in question.
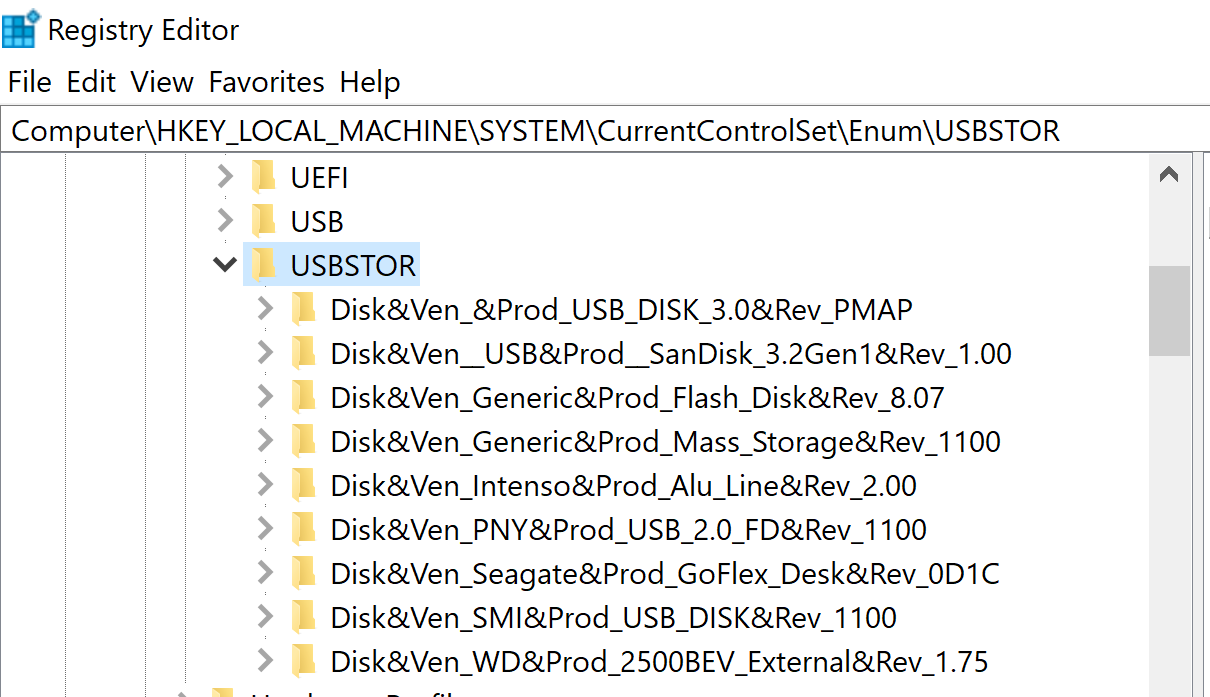
The key examples show use of “Intenso”, “Western Digital”, and “Seagate” vendors.
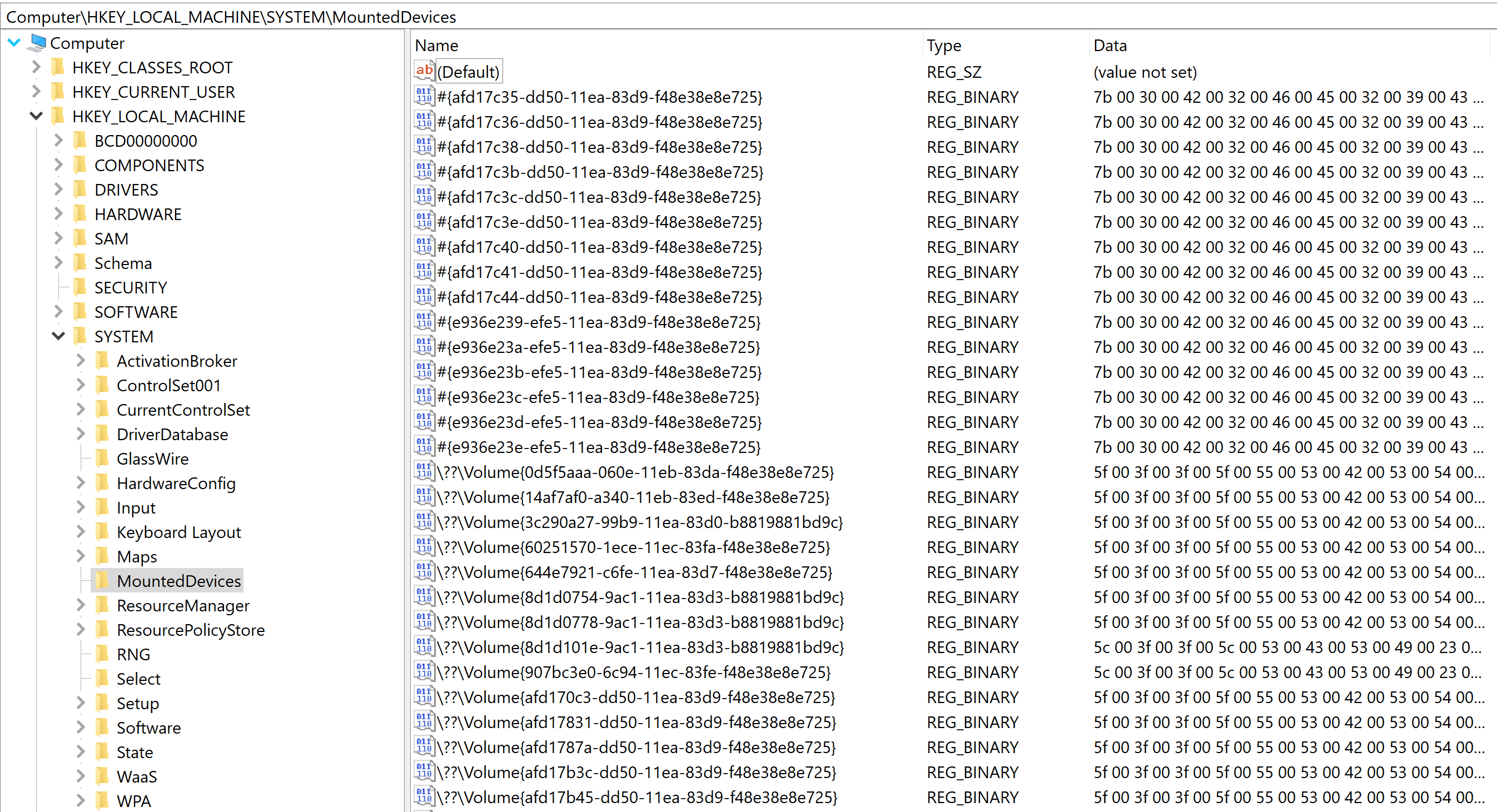
Next is reviewing the key values found in HKLM\SYSTEM\MountedDevices.
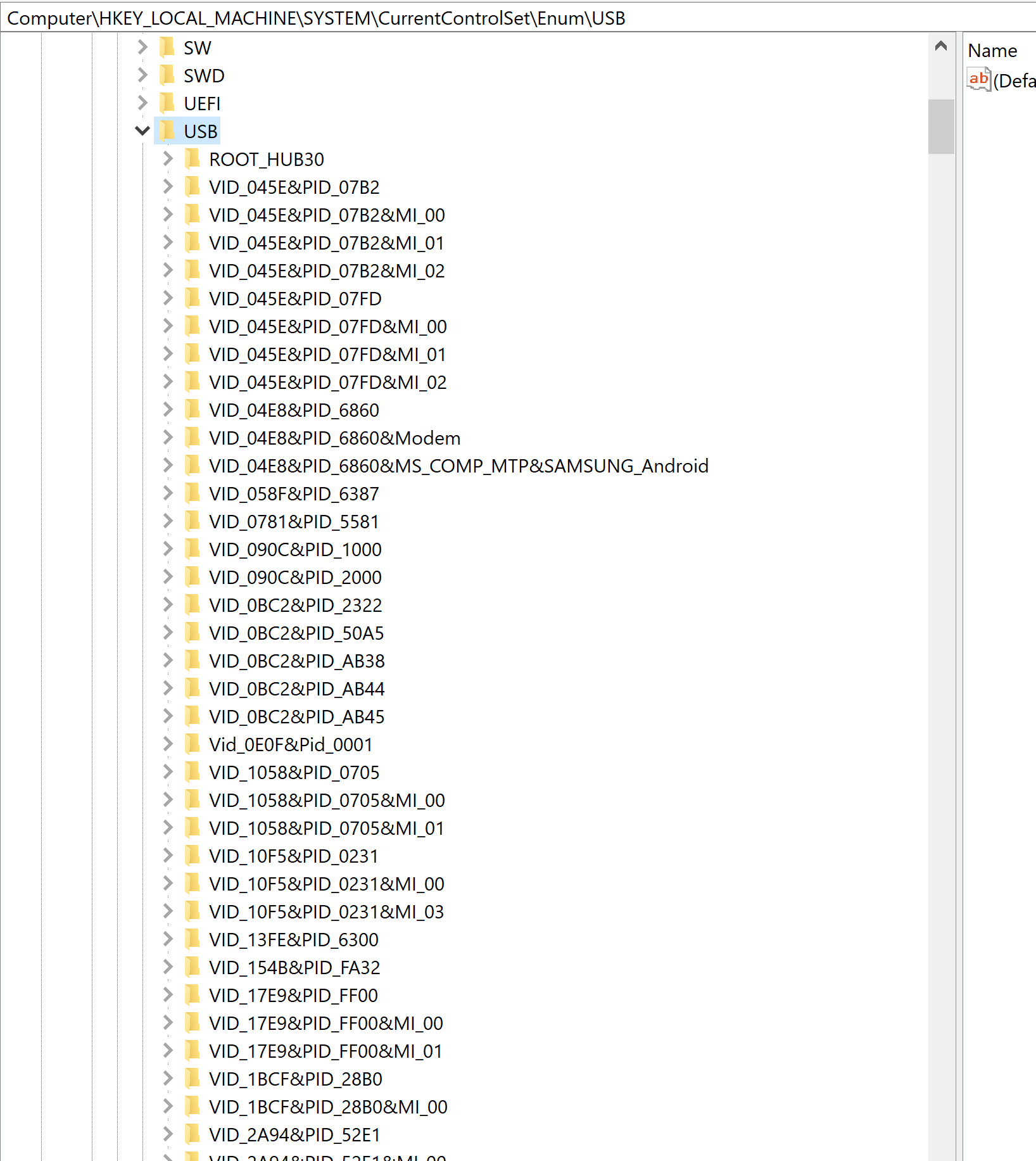
We review details found in HLKM\SYSTEM\CurrentControlSet\Enum\USB. We see the use of USB usage in general. This is not specific to the USB Storage Devices.
Another search done was to validate the existence of PCI or “Peripheral Component Interconnect”.
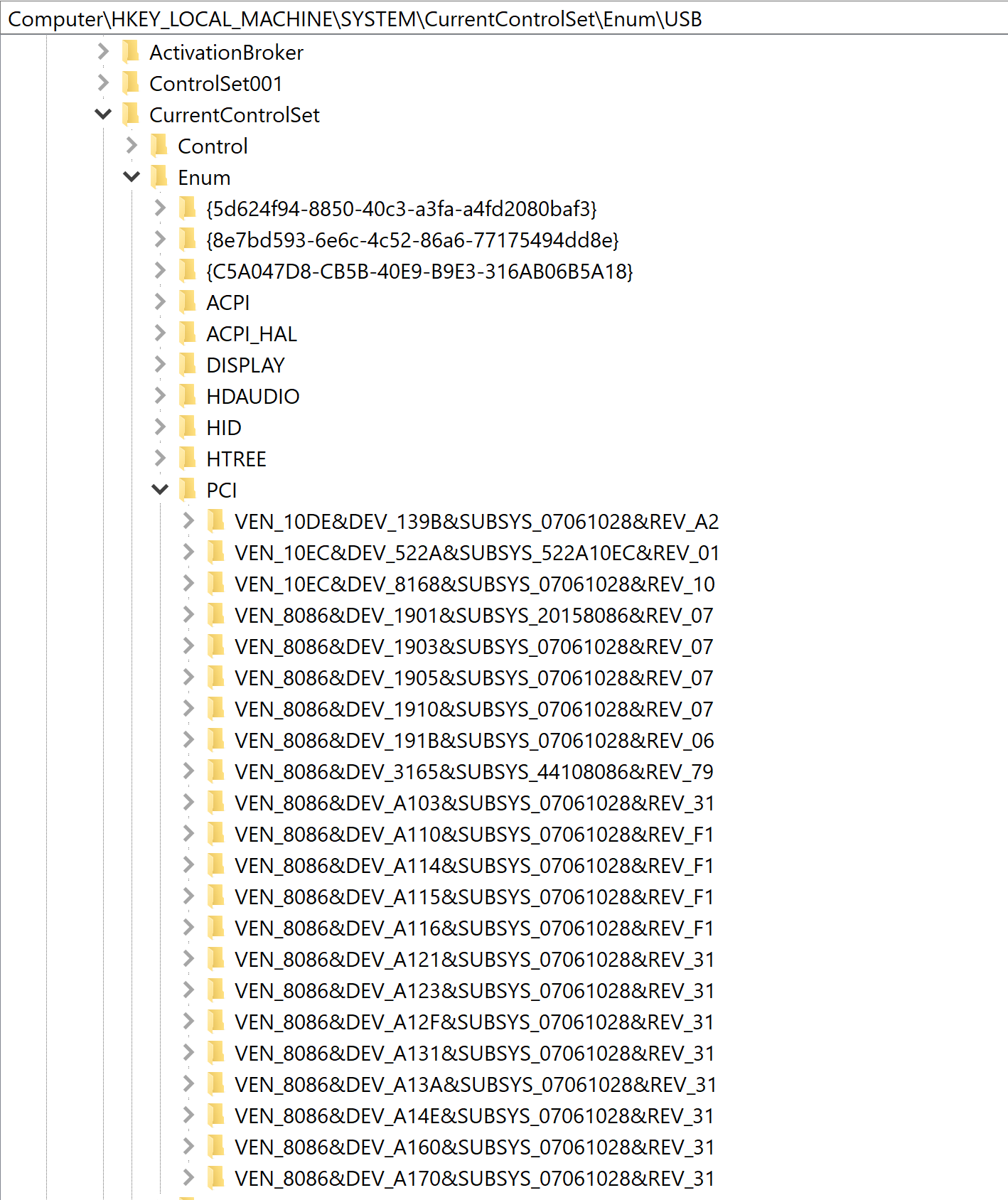
While not reviewed by documentation, it is an educated inference that USBSTOR refers to USB-based storage devices while USB covers anything that can be plugged via USB. This helps with differentiating if someone plugged in an unauthorized hardware because the focus tends to be in the “STORAGE”' aspects.
SD Card Artifacts Time
Unlike the USB-based removable media (found as subkey USBSTOR), SD card evidence will show up under the usage of subkey PCISTOR.
For the computer that was tested, while it had the capability to use SD cards, it had never had one plugged in. In order to validate that artifacts would not exist, I conducted a query for any signs of PCISTOR in the registry keys.
Results:
The next thing that I would do is plug in the SD Card into the computer for the first time. I recorded the timing that I plugged it in at 09:37 UTC.
I decided to do the search again. This time, below the highlighted PCI exists PCISTOR. This is now an indicator that the SD Card was plugged into the device.
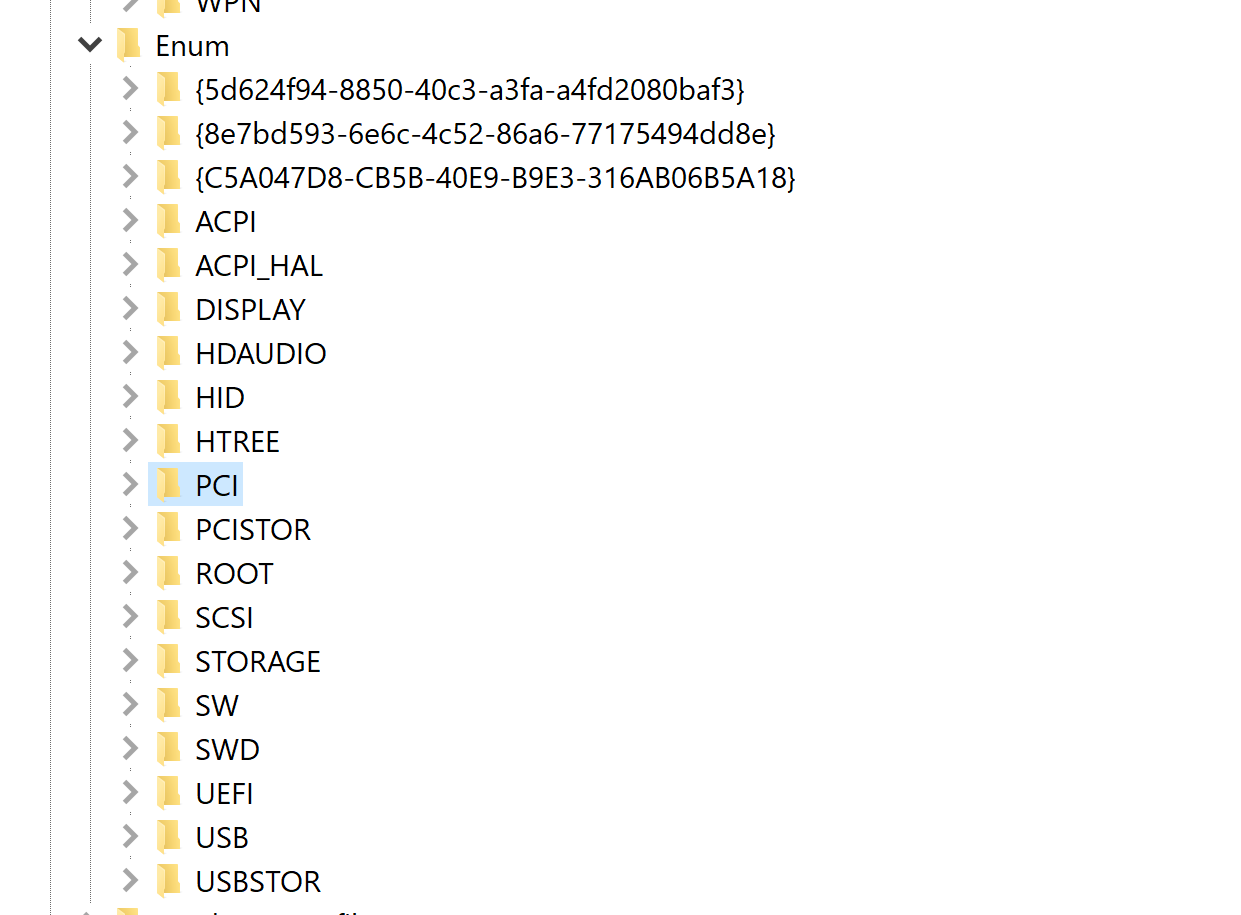
In this case, we find it in HKLM\SYSTEM\ControlSet001\Enum\PCISTOR
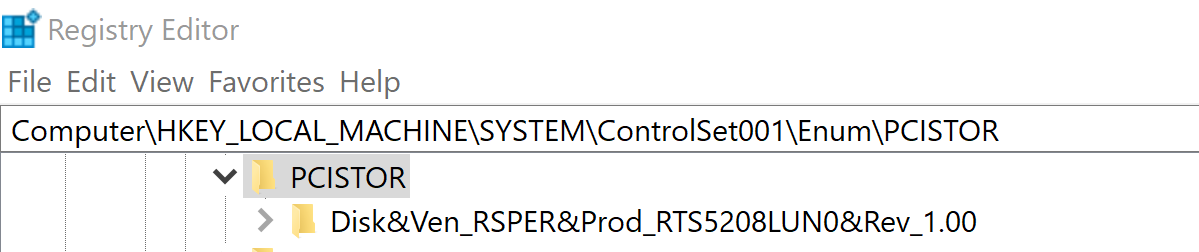
In order to do a deep dive on the registry key, I filtered down to see how far that I could go. There was one important observation that I noticed during my test and compared it to the case that I was working on.
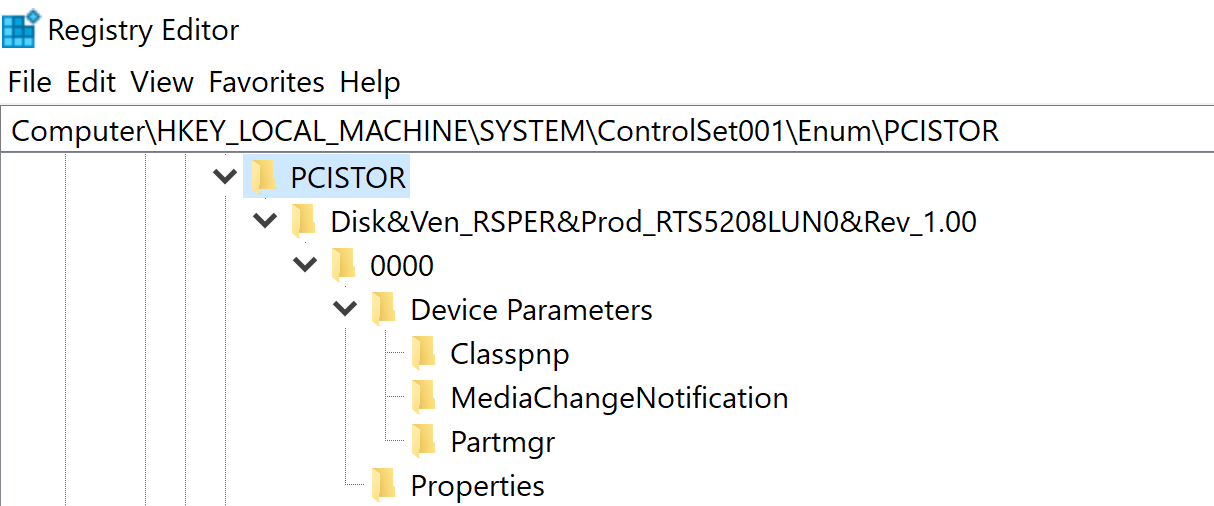
In this case, you will only get that the Vendor is “RSPER” and the product being “RTS5208LUN0”.
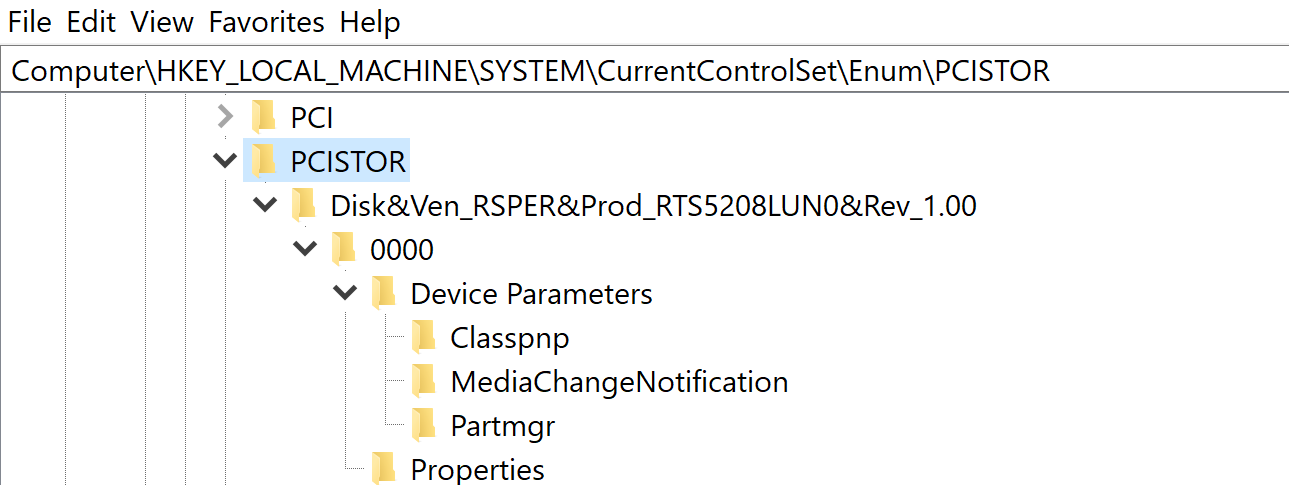
A quick query through Google shows that it relates to “Realtek RTS5208 Card Reader”. This is important to note because in comparison to the USBSTOR artifacts, which shows a more detailed information as to what was plugged in, all activity will only reference the Card Reader.
It is very unlikely to know what kind of SD card was used.
We return to HKLM\SYSTEM\MountedDevices in order to search for indicators that the SD Card was plugged in.
The initial review of the value \DosDevices\E: , we find indications related with the SD card use.
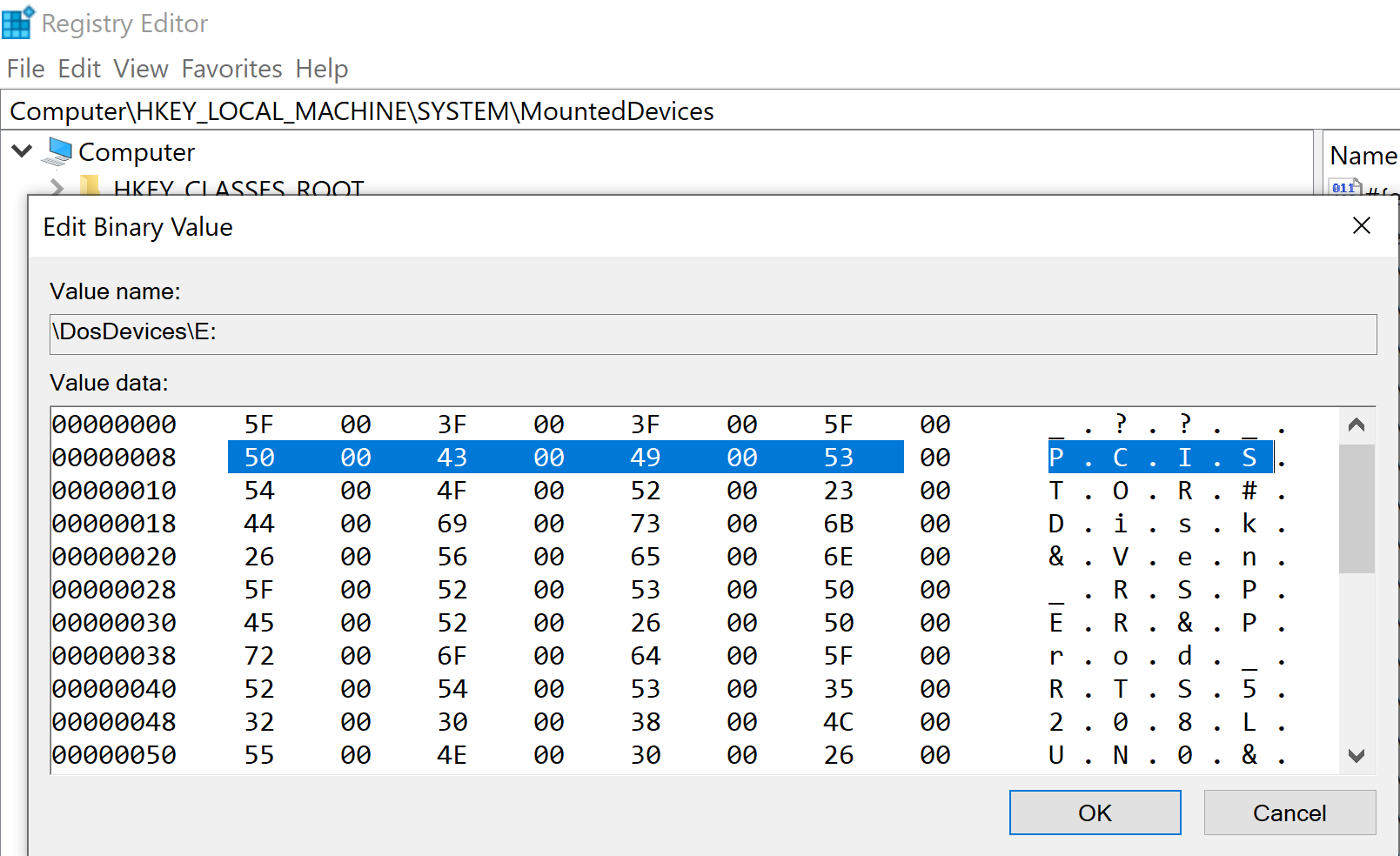
Within the data section, the hexadecimal indicator for PCISTOR, counting the nullbytes, is 500043004900530054004F0052 as seen below.
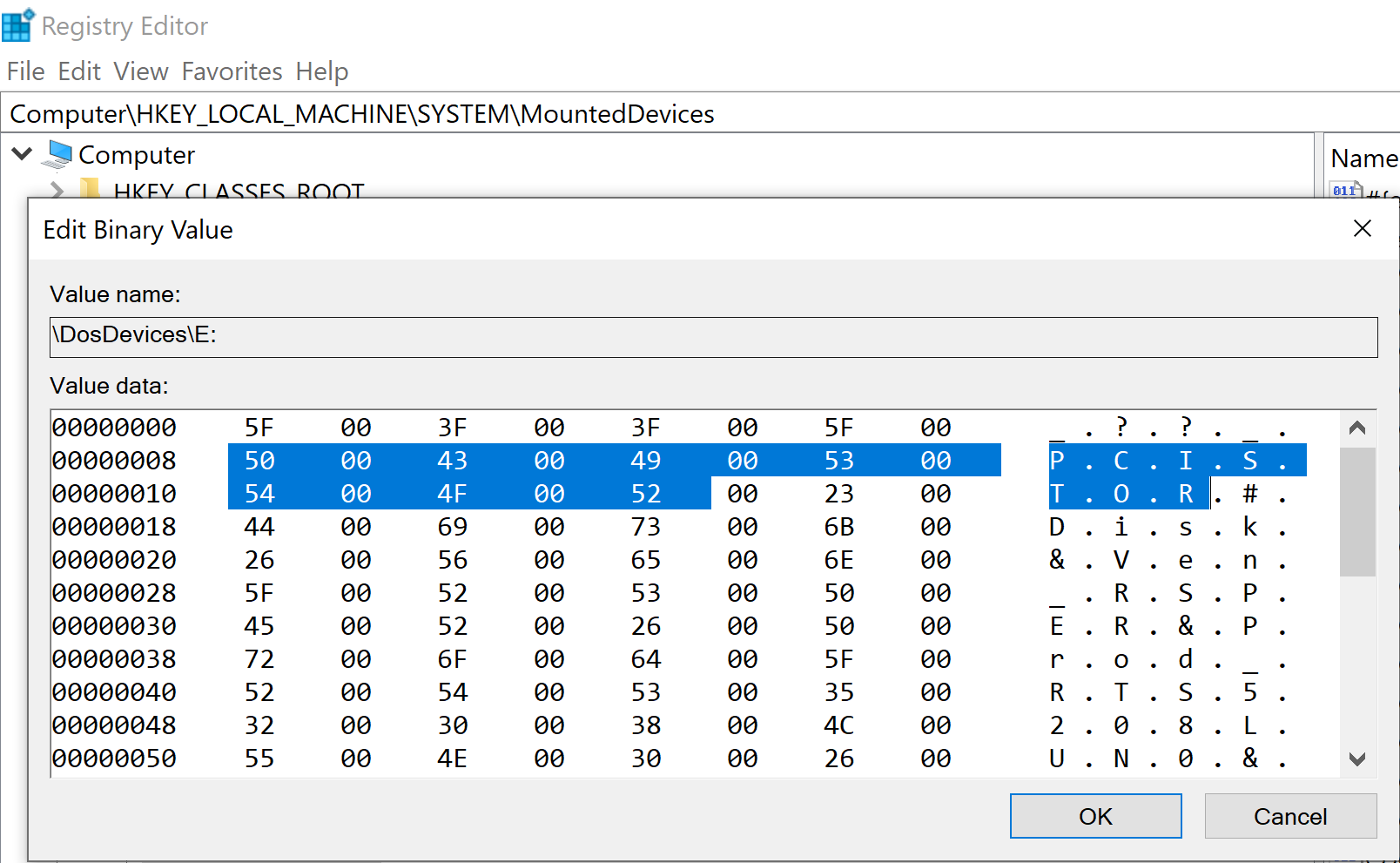
In the total search within the volume below, we do a full search of the related artfact: 5F003F003F005F00500043003900530054004F0052.
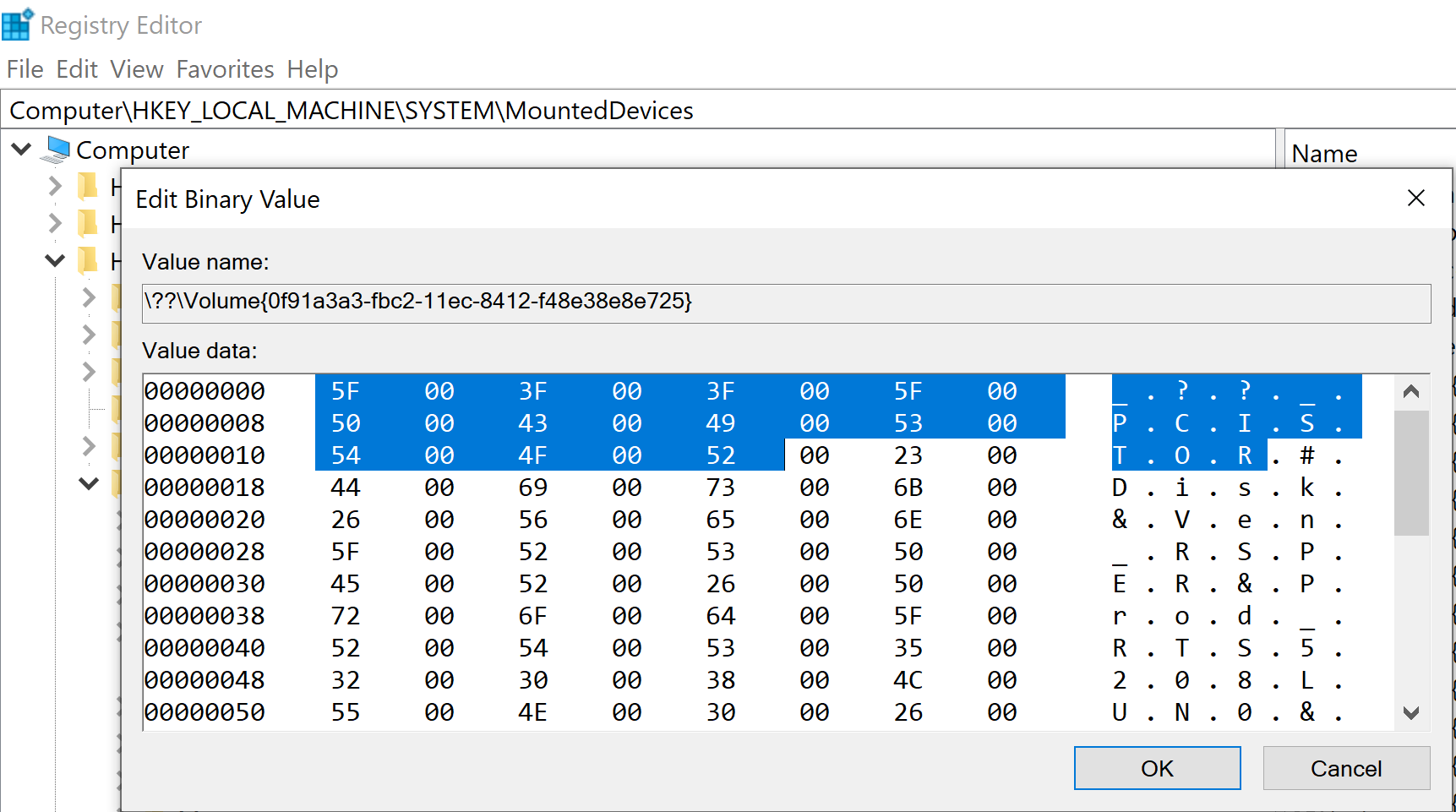
Beyond Registries
In addition to modifications in the registries, there is a log file, “setupapi.dev.log”, found in C:\Windows\INF.
The ‘Section Start’ time matched the time that I personally noted when I plugged in the device at 09:37 UTC. Upon initial review, the artifacts may likely be based on the System-designated Time Zone.
The timezone review may be worth for other analysts to validate.
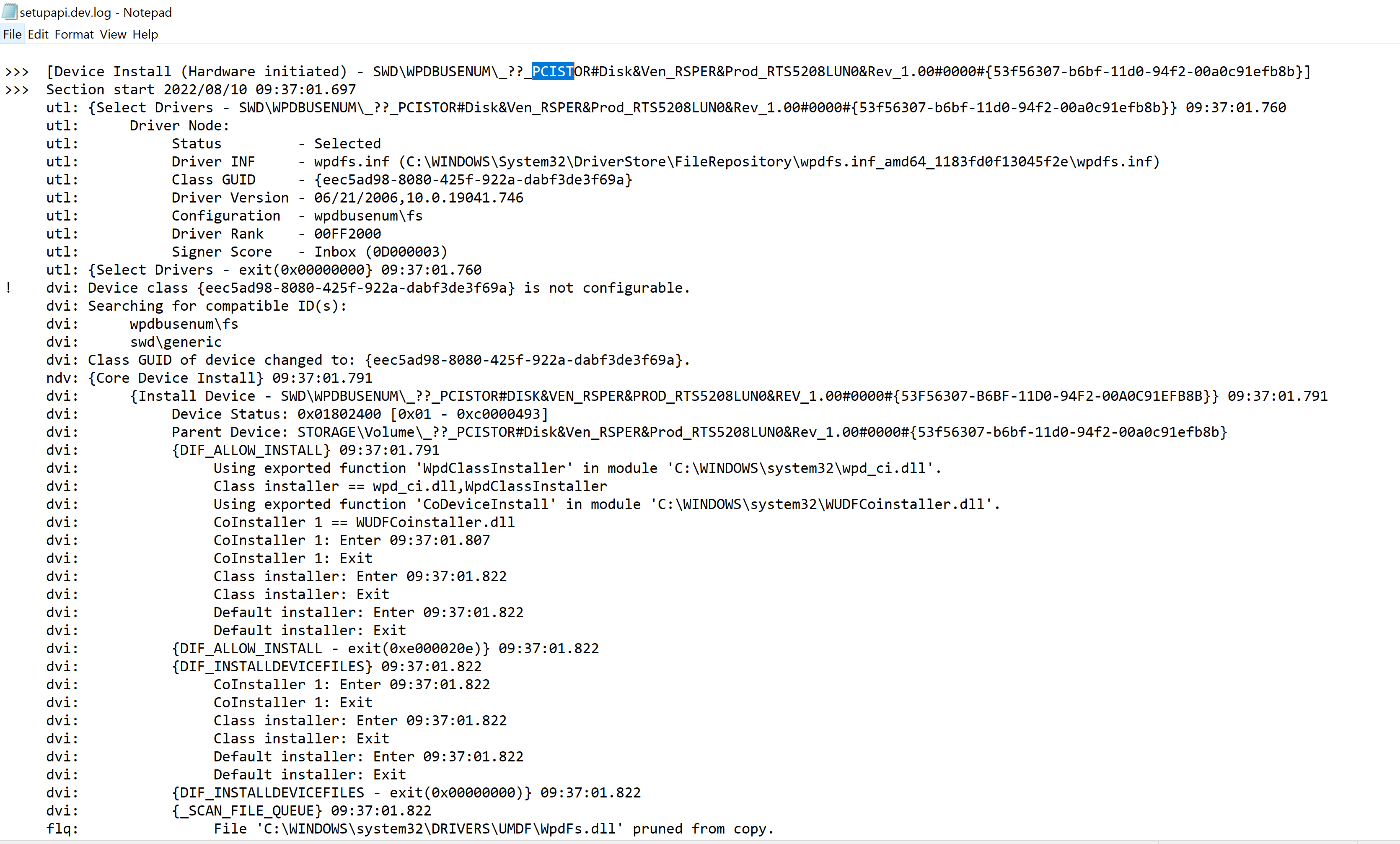
A caveat to investigating the “setupapi.dev.log” is that the data could potentially rotate as below.
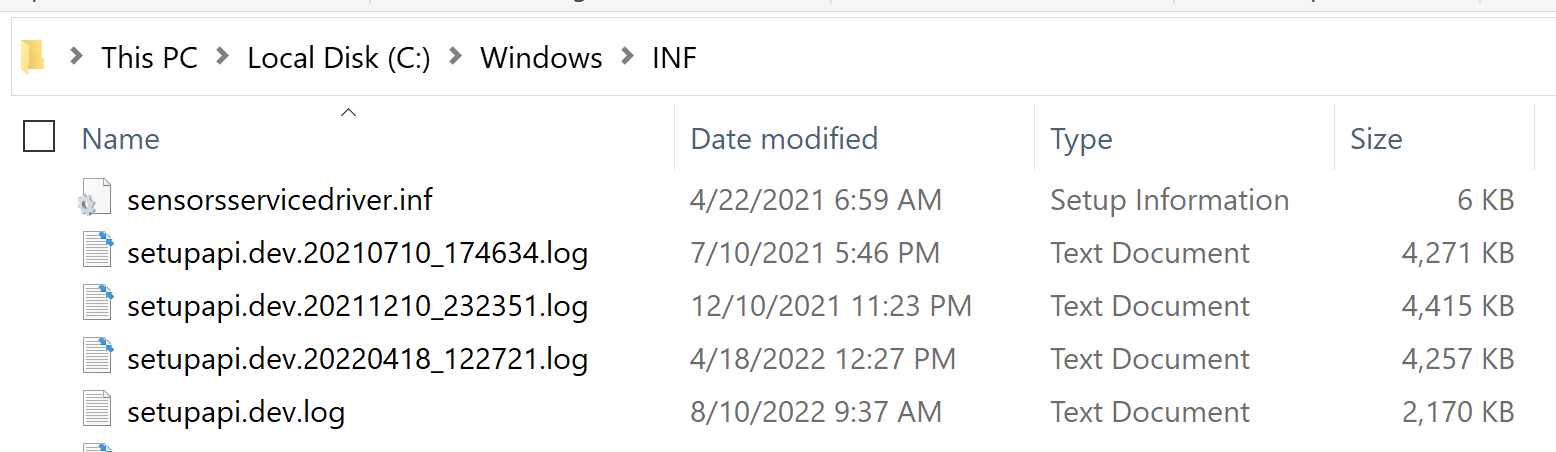
Initial review shows that it’s dated by YYYYMMDD_HHMMSS as to highlight when it was last modified. When collecting the logs, it is advisable to grab the others sorted in case the time found could exist in the other logs.
Key Takeaways
When investigating for evidence for usage of SD Cards, know that:
- Details on the evidence is not as prevalent as USB storage devices
- While principles are similar to USB-based storage devices (USBSTOR), it’s properties are different enough to warrant its own analysis
Sources
- Hassan, N.;Hijazi, R. (2017). Science Direct. “Data Hiding Forensics in Windows OS”. https://www.sciencedirect.com/topics/computer-science/windows-registry
- (2021, 02 June). Microsoft. Structure of the Registry. https://docs.microsoft.com/en-us/windows/win32/sysinfo/structure-of-the-registry
- (2009, 08 October). Microsoft. Overview of the Windows Registry. https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc781906(v=ws.10)